Blockchain technology what is – Blockchain technology: what is it? This revolutionary technology, underpinned by a decentralized and immutable ledger, is transforming industries. Its core lies in a chain of interconnected blocks, each securely storing data verified by a network of computers. This eliminates the need for central authorities, fostering trust and transparency across various applications, from cryptocurrencies to supply chain management.
Imagine a digital record-keeping system so secure and transparent that it’s practically tamper-proof. That’s the essence of blockchain. Each transaction is cryptographically secured and added to a chain of blocks, making it incredibly difficult to alter or delete information. This decentralized nature ensures that no single entity controls the data, leading to enhanced security and trust.
Defining Blockchain Technology
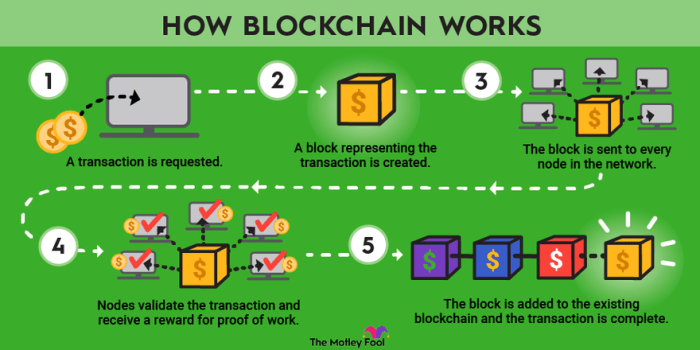
Blockchain technology is a revolutionary distributed ledger system that records and verifies transactions across multiple computers. Its core strength lies in its decentralized nature, eliminating the need for a central authority to manage and control the data. This inherent security and transparency make it suitable for a wide range of applications beyond cryptocurrencies, including supply chain management, healthcare, and voting systems.
Blockchain’s fundamental structure consists of interconnected blocks of data. Each block contains a timestamp, a hash (a unique digital fingerprint), and a set of validated transactions. This sequential linking of blocks, secured by cryptographic hashing, creates an immutable and auditable record.
Core Components of a Blockchain
A blockchain’s integrity depends on several key components working in concert. These components ensure the security, transparency, and immutability of the system. These components include:
- Blocks: These are containers holding batches of verified transactions. Each block is linked to the previous block via its hash, creating the chain.
- Hashing: A cryptographic function that converts data into a unique, fixed-size string of characters. Any change to the data results in a completely different hash, ensuring data integrity.
- Chain: The chronological sequence of blocks, linked together cryptographically. This chain forms the complete record of all transactions.
- Consensus Mechanism: A set of rules that governs how new blocks are added to the chain. Different mechanisms, such as Proof-of-Work or Proof-of-Stake, ensure the integrity and security of the blockchain.
- Nodes: Individual computers participating in the blockchain network. Nodes store a copy of the blockchain and participate in the consensus mechanism.
Adding a New Block to a Blockchain
The process of adding a new block involves several steps. First, transactions are broadcast to the network. Then, nodes collect these transactions and group them into a block. Next, a consensus mechanism (e.g., Proof-of-Work) verifies the transactions and ensures their validity. Once validated, the block is added to the chain, and its hash is linked to the previous block’s hash. This process ensures that once a block is added, it cannot be altered or removed without altering subsequent blocks and invalidating the entire chain.
Types of Blockchain Architectures
Blockchains can be categorized into different architectures based on their access control and permissioning models. Each architecture has its own strengths and weaknesses, making it suitable for different applications.
- Public Blockchains: These are permissionless blockchains, meaning anyone can participate in the network, view transactions, and add new blocks. Bitcoin and Ethereum are examples of public blockchains. Their transparency and decentralization are strengths, but they can be slower and less scalable than other types.
- Private Blockchains: These are permissioned blockchains, meaning access is restricted to authorized participants. A central authority controls access and permission to add blocks. Private blockchains offer greater control and faster transaction speeds but lack the transparency and decentralization of public blockchains. They are often used within organizations for internal record-keeping.
- Consortium Blockchains: These are permissioned blockchains where multiple organizations share control and governance. A group of participants jointly manages the network, balancing the benefits of permissioned and permissionless systems. Hyperledger Fabric is an example of a consortium blockchain. They offer a compromise between the centralized control of private blockchains and the decentralized nature of public blockchains.
Blockchain Analogy
Imagine a shared, tamper-proof digital ledger that records every transaction in a chronological and transparent manner. Each transaction is like a page in a book, and each block is a chapter containing multiple pages. Once a chapter is added to the book, it cannot be altered or removed. Many people have a copy of the entire book, and everyone can see the same information. This shared, transparent, and immutable record is the essence of a blockchain.
Blockchain Use Cases
Blockchain technology, while initially conceived for cryptocurrencies, has rapidly expanded its applications across diverse sectors. Its decentralized, transparent, and secure nature makes it a powerful tool for solving complex problems in various industries. This section will explore several key use cases demonstrating blockchain’s transformative potential.
Blockchain in Finance
Blockchain’s impact on the financial industry is profound. Its inherent security and efficiency are revolutionizing traditional processes. For instance, cross-border payments, often slow and expensive, can be significantly expedited and reduced in cost using blockchain-based platforms. These platforms eliminate intermediaries, reducing transaction fees and processing times. Furthermore, blockchain facilitates the creation of new financial instruments, such as security tokens representing ownership in assets, offering increased liquidity and transparency in capital markets. Companies like Ripple are leveraging blockchain for faster and cheaper international money transfers, while others are exploring its use in creating decentralized finance (DeFi) applications offering innovative lending and borrowing services.
Blockchain in Supply Chain Management
Supply chain management often suffers from a lack of transparency and traceability. Blockchain offers a solution by creating an immutable record of goods’ journey from origin to consumer. Each transaction, from raw material sourcing to final delivery, is recorded on the blockchain, providing complete visibility and accountability. This enhanced transparency reduces the risk of counterfeiting, improves product quality control, and streamlines logistics. For example, Walmart uses blockchain to track the origin and movement of its food products, enabling faster recall responses in case of contamination. Similarly, pharmaceutical companies are employing blockchain to monitor the distribution of drugs, ensuring authenticity and preventing the circulation of counterfeit medications.
Blockchain in Healthcare Data Management, Blockchain technology what is
The healthcare industry deals with sensitive patient data requiring stringent security and privacy measures. Blockchain can significantly enhance data management by providing a secure and transparent platform for storing and sharing medical records. Patient data can be encrypted and stored on the blockchain, granting patients control over access and sharing permissions. This system enhances patient privacy while facilitating seamless data exchange between healthcare providers, improving care coordination and reducing medical errors. While widespread adoption is still developing, several pilot projects demonstrate the potential of blockchain to improve patient data management and interoperability.
Blockchain in Digital Identity Verification
Digital identity verification is a crucial aspect of online security and trust. Blockchain can play a significant role in creating secure and verifiable digital identities. By storing identity information on a decentralized and immutable ledger, blockchain can prevent identity theft and fraud. Individuals can control their own data, and authorized parties can verify their identity without compromising privacy. This technology has the potential to streamline processes such as online banking, voting, and access control, significantly improving security and convenience. Several projects are exploring the use of blockchain-based digital identity systems, showcasing the potential for improved security and user control over personal data.
Understanding Cryptocurrencies
Cryptocurrencies are digital or virtual currencies designed to work as a medium of exchange. Their defining characteristic is their reliance on cryptography for security and to control the creation of new units, and to verify the transfer of funds. This cryptographic security is intrinsically linked to blockchain technology, making them inseparable.
Cryptocurrencies and blockchain technology share a symbiotic relationship. Blockchain acts as the distributed, immutable ledger that records all cryptocurrency transactions, ensuring transparency and preventing double-spending. Without blockchain’s secure and transparent record-keeping, cryptocurrencies would be vulnerable to fraud and manipulation. Conversely, the demand for cryptocurrencies drives the development and adoption of blockchain technology.
The Cryptocurrency Mining Process
Cryptocurrency mining is the process of verifying and adding new transactions to the blockchain. Miners use powerful computers to solve complex mathematical problems. The first miner to solve the problem adds the next block of transactions to the blockchain and is rewarded with newly minted cryptocurrency. This process secures the network and ensures the integrity of the blockchain. The difficulty of these problems adjusts automatically to maintain a consistent block creation rate, even as more miners join the network. This ensures the system remains secure and efficient.
Comparison of Cryptocurrency Consensus Mechanisms
Different cryptocurrencies employ various consensus mechanisms to validate transactions and add new blocks to the blockchain. Two prominent examples are Proof-of-Work (PoW) and Proof-of-Stake (PoS).
Proof-of-Work, used by Bitcoin, requires miners to expend significant computational power to solve complex cryptographic puzzles. The miner who solves the puzzle first adds the block and receives a reward. This mechanism is energy-intensive but provides a high level of security.
Proof-of-Stake, employed by Ethereum (since its transition) and many other cryptocurrencies, is a more energy-efficient alternative. Instead of relying on computational power, PoS selects validators based on the amount of cryptocurrency they hold (their “stake”). Validators propose and verify blocks, earning rewards based on their stake and performance. This mechanism reduces energy consumption while maintaining network security.
Comparison of Major Cryptocurrencies
The following table compares Bitcoin, Ethereum, and Solana, highlighting key differences:
| Cryptocurrency | Market Capitalization (Approximate) | Transaction Speed (Approximate) | Energy Consumption (Approximate) |
|---|---|---|---|
| Bitcoin (BTC) | USD $ Varies significantly | 7 transactions per second | High (PoW) |
| Ethereum (ETH) | USD $ Varies significantly | 15 transactions per second | Medium (PoS) |
| Solana (SOL) | USD $ Varies significantly | 2,000+ transactions per second | Low (PoH) |
Note: Market capitalization and transaction speeds fluctuate constantly. Energy consumption estimates are broad generalizations and can vary depending on various factors. Solana uses Proof of History (PoH), a different consensus mechanism than PoW or PoS.
Security and Privacy in Blockchain
Blockchain technology, while revolutionary, presents a complex interplay of enhanced security and potential privacy vulnerabilities. Its inherent design features contribute significantly to its robust security, yet the very nature of some blockchain implementations can raise concerns about data privacy. Understanding this duality is crucial for a comprehensive assessment of its overall impact.
Blockchain’s security is fundamentally rooted in its cryptographic architecture and decentralized nature. This combination creates a system that is resistant to many traditional forms of attack.
Immutability and Cryptographic Hashing
Immutability, a cornerstone of blockchain security, refers to the inability to alter or delete previously recorded data. Each block in the chain contains a cryptographic hash – a unique fingerprint – of the previous block’s data. Altering any data within a block would change its hash, creating an inconsistency and immediately invalidating the entire chain beyond that point. This makes tampering extremely difficult and detectable. The cryptographic hashing algorithms used, such as SHA-256, are computationally intensive, making brute-force attacks impractical. This chain of interconnected, cryptographically secured blocks ensures data integrity and prevents unauthorized modifications.
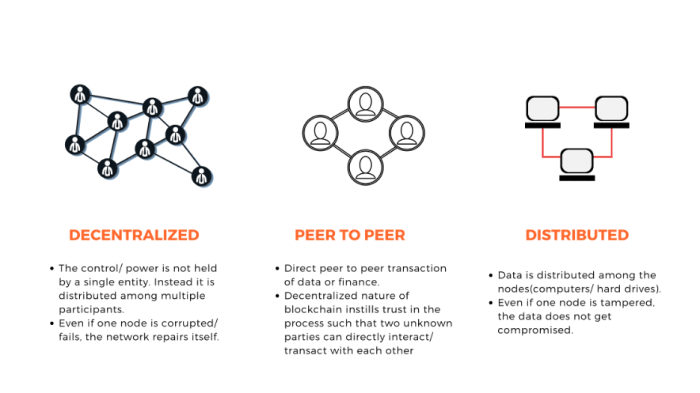
Decentralization and Consensus Mechanisms
The decentralized nature of blockchain, where data is distributed across a network of nodes, further enhances security. There’s no single point of failure, making it highly resistant to attacks targeting a central server. Consensus mechanisms, such as Proof-of-Work (PoW) or Proof-of-Stake (PoS), ensure that new blocks are added to the chain only after validation by a significant portion of the network. This distributed validation process makes it extremely difficult for a single entity or group to manipulate the blockchain. For example, in a PoW system, the computational power required to overcome the network’s collective hashing power is prohibitively expensive and time-consuming.
Potential Vulnerabilities
While blockchain boasts significant security features, it is not invulnerable. Potential vulnerabilities exist, primarily focusing on the implementation and management of blockchain systems. 51% attacks, where a single entity controls more than half of the network’s computing power, represent a significant threat. Such an attack could allow the malicious actor to reverse transactions or introduce fraudulent blocks. Furthermore, smart contract vulnerabilities, arising from coding errors or design flaws within smart contracts, can be exploited to drain funds or manipulate data. Weaknesses in the cryptographic algorithms themselves, though rare, could also compromise the system’s security. Finally, external factors like compromised private keys or phishing attacks targeting users remain a significant risk.
Privacy Concerns in Public Blockchains
Public blockchains, by design, offer transparency. All transactions are recorded and publicly viewable. While pseudonymous (using addresses instead of names), the association of addresses with real-world identities can potentially compromise user privacy. Sophisticated analysis techniques can be used to link transactions to individuals, revealing sensitive financial information or patterns of behavior. This lack of inherent privacy in public blockchains is a significant consideration for applications requiring confidential data handling. Privacy-enhancing technologies, such as zero-knowledge proofs and confidential transactions, are being developed to address these concerns.
Scalability and Efficiency
Blockchain technology, while revolutionary, faces significant hurdles in achieving widespread adoption. Its inherent design, prioritizing security and decentralization, often clashes with the need for high transaction throughput and speed required by large-scale applications. This section delves into the challenges of scaling blockchain and explores various solutions aiming to improve both scalability and energy efficiency.
The core challenge lies in the fundamental trade-off between decentralization, security, and scalability. Maintaining a truly decentralized network where all nodes validate every transaction ensures security but significantly limits transaction speeds. As the number of transactions increases, the network becomes congested, leading to increased transaction fees and slower confirmation times. This limitation hinders the adoption of blockchain for applications requiring high transaction volumes, such as payment systems handling millions of transactions daily.
Sharding
Sharding is a technique that partitions the blockchain into smaller, more manageable pieces called “shards.” Each shard processes a subset of transactions, effectively distributing the workload across multiple nodes. This parallel processing significantly increases transaction throughput. For example, a blockchain using sharding could process transactions many times faster than a monolithic blockchain of the same size. However, implementing sharding requires careful consideration of data consistency and cross-shard communication to maintain the integrity of the overall blockchain. It also introduces complexities in managing shard assignments and ensuring fairness in transaction distribution.
Layer-2 Solutions
Layer-2 scaling solutions operate on top of the main blockchain (Layer-1), handling a significant portion of transactions off-chain. This reduces the load on the main blockchain, improving scalability without compromising security. Popular Layer-2 solutions include state channels, sidechains, and rollups. State channels allow participants to conduct multiple transactions off-chain, settling only the net result on the main chain. Sidechains offer a separate blockchain parallel to the main chain, enabling faster and cheaper transactions. Rollups bundle multiple transactions into a single transaction on the main chain, significantly reducing the number of individual transactions processed. Each of these solutions offers a unique trade-off between speed, cost, and complexity. For instance, state channels are highly efficient for frequent transactions between the same parties, while rollups are better suited for handling a large number of transactions from various sources.
Energy Efficiency of Consensus Mechanisms
Different blockchain consensus mechanisms vary significantly in their energy consumption. Proof-of-Work (PoW), famously used by Bitcoin, requires extensive computational power, leading to high energy consumption. Proof-of-Stake (PoS), employed by many newer blockchains like Ethereum 2.0, is significantly more energy-efficient as it relies on validators staking their cryptocurrency instead of competing in a computational race. Other mechanisms like Delegated Proof-of-Stake (DPoS) and Practical Byzantine Fault Tolerance (PBFT) further reduce energy consumption by limiting the number of validators involved in consensus. The energy efficiency of a blockchain directly impacts its environmental footprint and operational costs. The shift towards PoS and other energy-efficient mechanisms is a crucial step in making blockchain technology more sustainable.
Factors Impacting Blockchain Transaction Speed
Several factors influence the speed of blockchain transactions. These include:
- Block size: Larger block sizes allow more transactions to be included in each block, increasing throughput.
- Block time: Shorter block times lead to faster transaction confirmation.
- Network congestion: High network traffic can slow down transaction processing.
- Consensus mechanism: The chosen consensus mechanism significantly impacts transaction speed.
- Transaction complexity: More complex transactions require more processing time.
- Node performance: The processing power and network connectivity of individual nodes influence overall network performance.
Optimizing these factors is critical for improving blockchain transaction speed and overall efficiency. For instance, increasing block size or reducing block time can directly improve transaction throughput, while implementing more efficient consensus mechanisms can reduce the computational overhead.
Decentralization and Governance
Decentralization is a cornerstone of blockchain technology, differentiating it from traditional centralized systems. It implies a distributed network where no single entity controls the data or the network’s operations. This inherent characteristic fosters trust, transparency, and resilience, mitigating single points of failure and censorship. This section explores the concept of decentralization within blockchain, examining its mechanisms and the challenges associated with governing such systems.
Decentralization in blockchain is achieved through a distributed ledger technology (DLT). Instead of relying on a central authority to validate and record transactions, blockchain uses a network of nodes, each maintaining a copy of the entire blockchain. This distributed nature ensures that no single entity has complete control, promoting data integrity and resistance to manipulation. The level of decentralization can vary, however, depending on the specific blockchain’s architecture and the distribution of nodes. Highly decentralized blockchains have a large number of geographically dispersed nodes, each with equal power and influence.
Consensus Mechanisms
Consensus mechanisms are crucial for maintaining decentralization and ensuring the integrity of the blockchain. They establish rules for validating and adding new blocks of transactions to the chain. Different mechanisms offer varying trade-offs between speed, security, and energy consumption. Proof-of-Work (PoW), famously used by Bitcoin, requires nodes to solve complex computational problems to validate transactions, ensuring security but consuming significant energy. Proof-of-Stake (PoS), employed by Ethereum and many other blockchains, assigns validation rights based on the amount of cryptocurrency staked by a node, offering a more energy-efficient alternative. Other mechanisms, like Delegated Proof-of-Stake (DPoS) and Practical Byzantine Fault Tolerance (PBFT), offer further variations in the approach to consensus. The choice of consensus mechanism significantly impacts the blockchain’s overall characteristics and its level of decentralization.
Governance Challenges in Decentralized Networks
Governing decentralized blockchain networks presents unique challenges. The absence of a central authority necessitates the development of robust and transparent governance mechanisms to resolve disputes, upgrade the protocol, and manage the network’s evolution. Reaching consensus among a large and diverse group of participants can be difficult and time-consuming. Furthermore, the risk of network fragmentation due to disagreements over governance decisions is a significant concern. Sybil attacks, where malicious actors create numerous fake identities to gain undue influence, also pose a threat to the network’s integrity and decentralized nature. Balancing the need for efficient decision-making with the principles of decentralization is a continuous challenge.
Blockchain Governance Models
Various models exist for governing decentralized blockchain networks. These models differ in how decisions are made and how power is distributed among participants. Some networks utilize a purely decentralized model, where all participants have an equal say in governance decisions through voting mechanisms. Others employ a more centralized approach, with a smaller group of developers or stakeholders holding significant influence. Hybrid models combine elements of both approaches, attempting to balance decentralization with the need for efficient decision-making. The choice of governance model depends on the specific needs and goals of the blockchain network. For instance, a blockchain aiming for maximum decentralization might opt for a purely decentralized model, while a blockchain prioritizing scalability and efficiency might choose a more centralized approach. The optimal governance model is often a subject of ongoing debate and experimentation within the blockchain community.
Smart Contracts
Smart contracts are self-executing contracts with the terms of the agreement between buyer and seller being directly written into lines of code. This code resides on a blockchain, ensuring transparency, immutability, and automation of the agreement. Instead of relying on intermediaries to enforce the contract, the blockchain itself acts as the guarantor, triggering actions automatically upon the fulfillment of pre-defined conditions. This eliminates the need for trust in a central authority, making them particularly useful in situations where multiple parties need to interact securely and efficiently.
Smart contracts leverage the inherent properties of blockchain technology – decentralization, transparency, and security – to create a more efficient and trustworthy system for managing agreements. Their potential spans numerous industries, revolutionizing how we conduct business and interact in the digital world.
Smart Contract Applications Across Industries
Smart contracts find practical application in diverse sectors. Their automation and security features offer significant advantages.
- Supply Chain Management: Tracking goods from origin to consumer, ensuring authenticity and preventing counterfeiting. Imagine a scenario where a shipment of pharmaceuticals is tracked on a blockchain, with smart contracts automatically releasing payment to the supplier upon verification of delivery and quality checks at each stage.
- Insurance: Automating claims processing based on predefined criteria. For example, a smart contract could automatically pay out a claim for car insurance upon confirmation of an accident via connected car technology and verification of damages.
- Healthcare: Securely storing and managing patient medical records, with controlled access granted via smart contracts. This could improve data privacy and streamline the sharing of information between healthcare providers.
- Real Estate: Facilitating property transactions by automating escrow payments and title transfers. A smart contract could hold the funds until all conditions of the sale are met, ensuring both buyer and seller are protected.
- Digital Identity: Verifying and managing digital identities, reducing fraud and improving security. Smart contracts could manage access to sensitive data based on verified identity credentials.
Legal and Regulatory Implications of Smart Contracts
The legal framework surrounding smart contracts is still evolving. Questions of jurisdiction, contract enforceability, and liability remain largely unaddressed in many legal systems. The decentralized nature of blockchain presents challenges for traditional legal processes. Ensuring the clarity and enforceability of smart contract terms is crucial. Furthermore, addressing potential vulnerabilities in the code and preventing malicious actors from exploiting them is paramount. The legal implications will continue to be refined as the technology matures and its use becomes more widespread.
A Simple Smart Contract Scenario and Implementation
Consider a simple escrow system for a digital art sale. The buyer deposits funds into a smart contract, and the seller releases the artwork upon verification of payment. The smart contract code would include conditions: if payment is confirmed, release the artwork to the buyer; if payment is not received within a specified time, return the funds to the buyer. This simple scenario illustrates how smart contracts can automate trustless transactions. Implementation would involve writing the contract in a suitable language like Solidity (for Ethereum) or similar, deploying it to a blockchain, and then interacting with it through an interface. The code would be publicly viewable on the blockchain, ensuring transparency and accountability.
The Future of Blockchain Technology
Blockchain technology, while still relatively nascent, is poised for significant growth and evolution over the next decade. Its inherent capabilities for secure, transparent, and decentralized data management are attracting increasing attention across diverse sectors, leading to predictions of transformative impacts on various industries. However, challenges remain in terms of scalability, regulation, and public understanding.
Predicted Developments in Blockchain Technology
Several key advancements are anticipated in the near future. We can expect to see significant improvements in scalability through the implementation of layer-2 solutions and advancements in consensus mechanisms. For example, sharding, a technique that divides the blockchain into smaller, more manageable parts, is already being implemented in various blockchain networks to enhance transaction throughput. Furthermore, the development of more energy-efficient consensus algorithms, such as Proof-of-Stake, will address environmental concerns associated with some current blockchain implementations. The integration of artificial intelligence (AI) and machine learning (ML) is also likely to play a crucial role, optimizing processes and enhancing the overall efficiency of blockchain networks. This includes automated smart contract creation and execution, as well as improved fraud detection and prevention.
Emerging Use Cases for Blockchain
Beyond its current applications in cryptocurrencies and supply chain management, blockchain’s potential extends to numerous other fields. In healthcare, blockchain could revolutionize data management and patient privacy, allowing for secure sharing of medical records between providers while maintaining patient control. In the voting system, blockchain could enhance transparency and security, reducing the risk of fraud and manipulation. Furthermore, the decentralized nature of blockchain could foster greater trust and efficiency in digital identity management, providing individuals with more control over their personal data. The development of decentralized autonomous organizations (DAOs) will also further expand the application of blockchain in governance and management. For instance, a DAO could manage a shared resource, such as a renewable energy grid, in a transparent and community-driven manner.
Obstacles to Widespread Adoption
Despite its potential, several factors could hinder the widespread adoption of blockchain technology. Regulatory uncertainty remains a significant obstacle, with governments grappling with how to effectively regulate cryptocurrencies and blockchain-based applications. The complexity of blockchain technology can also pose a barrier to entry for businesses and individuals lacking the technical expertise to implement and utilize it effectively. Furthermore, the lack of interoperability between different blockchain networks limits their potential for widespread adoption. A lack of standardized protocols and frameworks could impede seamless data exchange and integration across different platforms. Finally, addressing public perception and building trust are crucial for the successful adoption of blockchain technology. Overcoming misinformation and fostering greater understanding of its benefits are vital steps towards widespread acceptance.
Impact on Various Industries (5-10 Years)
Over the next five to ten years, blockchain is projected to significantly impact various industries. In finance, blockchain could streamline cross-border payments, reduce transaction costs, and enhance security. Examples include Ripple’s efforts in facilitating faster and cheaper international payments. In supply chain management, blockchain can provide greater transparency and traceability, improving efficiency and reducing counterfeiting. Walmart, for example, uses blockchain to track the origin and movement of its food products. In the energy sector, blockchain could facilitate peer-to-peer energy trading, promoting greater efficiency and sustainability. In digital identity, blockchain-based solutions could provide individuals with more control over their personal data, reducing the risk of identity theft and fraud. These examples illustrate the potential for transformative change across numerous sectors.
Illustrating a Blockchain Transaction
A blockchain transaction represents the transfer of value or data from one party to another, recorded immutably on a distributed ledger. This process involves several key steps and components, ensuring transparency and security. Let’s examine a simplified example to understand the mechanics.
Imagine Alice wants to send Bob 5 Bitcoin (BTC). This seemingly simple action involves a complex series of steps within the blockchain network. The transaction is not directly transferred between Alice and Bob; rather, it’s verified and added to the blockchain by a network of computers (nodes).
Blockchain technology, at its core, is a decentralized, secure ledger system. Its applications are vast, extending beyond cryptocurrencies to areas like supply chain management and even aerospace. For example, consider how companies like united aerospace technologies could leverage blockchain for enhanced transparency and security in their operations. Ultimately, the potential of blockchain technology to revolutionize various industries remains largely untapped.
Transaction Initiation
Alice initiates the transaction by creating a digitally signed message. This message contains details such as the sender’s address (Alice’s), the receiver’s address (Bob’s), the amount of BTC (5), and a transaction fee paid to miners for processing the transaction. This message is cryptographically signed using Alice’s private key, proving her authorization.
Broadcast to the Network
This signed transaction message is then broadcast to the network of nodes. The nodes are computers running blockchain software that participate in the validation and addition of transactions to the blockchain.
Verification and Validation
Nodes verify the transaction’s validity by checking:
- Alice’s digital signature: Confirming the transaction’s authenticity and preventing unauthorized spending.
- Alice’s sufficient balance: Ensuring she has enough BTC to make the transfer.
- Transaction fee: Confirming payment for processing the transaction.
This verification process is crucial for maintaining the integrity of the blockchain.
Blockchain technology, at its core, is a decentralized, secure ledger system. Its applications are vast, extending beyond cryptocurrencies to areas like supply chain management and even aerospace. For example, consider how companies like united aerospace technologies could leverage blockchain for enhanced transparency and security in their operations. Ultimately, the potential of blockchain technology to revolutionize various industries remains largely untapped.
Block Creation and Addition
Once a sufficient number of nodes validate the transaction, it’s grouped with other validated transactions into a “block.” This block includes a timestamp, a cryptographic hash of the previous block (linking it to the chain), and the hash of the transactions within the block. The process of adding a block to the chain is known as “mining,” and typically involves solving complex cryptographic puzzles.
Block Confirmation
After a block is added to the blockchain, the transaction is considered confirmed. The number of confirmations required varies depending on the specific blockchain, but generally, more confirmations mean greater security. Once confirmed, the transaction is permanently recorded on the distributed ledger, visible to all participants.
Visual Representation
- Alice (Sender): Possesses 10 BTC and initiates a transaction to send 5 BTC to Bob.
- Transaction Data: Includes Alice’s address, Bob’s address, amount (5 BTC), and transaction fee.
- Digital Signature: Alice signs the transaction using her private key.
- Broadcast: The signed transaction is broadcast to the network of nodes.
- Verification: Nodes verify the signature, Alice’s balance, and the transaction fee.
- Block Creation: The validated transaction is added to a block with other transactions.
- Block Addition: The block is added to the blockchain after the mining process.
- Bob (Receiver): Receives 5 BTC after the transaction is confirmed.
Comparing Blockchain with Traditional Databases
Blockchain technology and traditional centralized databases represent fundamentally different approaches to data management. While both store and manage information, their architectures, security models, and functionalities differ significantly, impacting their suitability for various applications. This comparison highlights key distinctions between these two systems.
Understanding these differences is crucial for choosing the appropriate technology for a given task. A centralized database might be ideal for applications requiring high transaction speeds and simple data structures, while a blockchain’s decentralized and immutable nature makes it more suitable for applications demanding high security and transparency.
Data Security
The security models of blockchain and traditional databases differ drastically. Centralized databases rely on robust security measures implemented at the server level, such as firewalls, access controls, and encryption. However, a single point of failure exists – the central server. A breach of this server compromises the entire database. Blockchain, on the other hand, distributes data across numerous nodes. This decentralized architecture makes it significantly more resistant to attacks, as compromising the entire system requires compromising a vast majority of the nodes simultaneously, a highly improbable feat.
- Traditional Databases: Centralized security, single point of failure, susceptible to large-scale data breaches if the central server is compromised.
- Blockchain: Decentralized security, distributed ledger, requires compromising a majority of nodes for a successful attack, significantly increasing resilience.
Data Transparency
Transparency levels also differ markedly. Traditional databases typically operate with restricted access, controlled by administrators who determine which users can view and modify data. Blockchain, conversely, often prioritizes transparency. While the level of transparency can be adjusted depending on the specific implementation (e.g., public vs. private blockchain), the underlying principle is that all participants in the network can view the transaction history, enhancing accountability and trust.
- Traditional Databases: Data access is controlled by administrators; transparency is limited to authorized users only.
- Blockchain: Depending on the type of blockchain, data can be publicly viewable (with appropriate hashing to protect personal information), fostering greater transparency and auditability.
Data Efficiency
Efficiency considerations vary significantly between blockchain and traditional databases. Traditional databases, particularly relational databases, are optimized for rapid data retrieval and modification. Complex queries can be executed efficiently. Blockchain, however, is inherently slower due to the consensus mechanisms required to validate and add new blocks to the chain. The added security comes at the cost of speed. While improvements are continuously being made to increase blockchain efficiency, it still lags behind traditional databases in terms of raw transaction throughput.
- Traditional Databases: Optimized for speed and efficiency in data retrieval and modification; capable of handling high transaction volumes.
- Blockchain: Slower transaction speeds due to consensus mechanisms; scalability remains a challenge, though improvements are ongoing.
Final Wrap-Up: Blockchain Technology What Is
In conclusion, blockchain technology represents a paradigm shift in data management and security. While challenges remain, particularly regarding scalability and regulation, its potential to revolutionize various sectors is undeniable. From enhancing financial transactions to improving supply chain efficiency and revolutionizing healthcare data management, blockchain’s impact is only just beginning to be felt. Its inherent security and transparency offer a compelling alternative to traditional centralized systems, promising a more trustworthy and efficient future.





